
Downloads:
5,091
Downloads of v 8.3.0:
42
Last Update:
26 May 2025
Package Maintainer(s):
Software Author(s):
- Robin Granberg
Tags:
- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
AD ACL Scanner (Script)
- 1
- 2
- 3
8.3.0 | Updated: 26 May 2025
- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
Downloads:
5,091
Downloads of v 8.3.0:
42
Maintainer(s):
Software Author(s):
- Robin Granberg
AD ACL Scanner (Script) 8.3.0
Legal Disclaimer: Neither this package nor Chocolatey Software, Inc. are affiliated with or endorsed by Robin Granberg. The inclusion of Robin Granberg trademark(s), if any, upon this webpage is solely to identify Robin Granberg goods or services and not for commercial purposes.
- 1
- 2
- 3
All Checks are Passing
3 Passing Tests
Deployment Method: Individual Install, Upgrade, & Uninstall
To install AD ACL Scanner (Script), run the following command from the command line or from PowerShell:
To upgrade AD ACL Scanner (Script), run the following command from the command line or from PowerShell:
To uninstall AD ACL Scanner (Script), run the following command from the command line or from PowerShell:
Deployment Method:
This applies to both open source and commercial editions of Chocolatey.
1. Enter Your Internal Repository Url
(this should look similar to https://community.chocolatey.org/api/v2/)
2. Setup Your Environment
1. Ensure you are set for organizational deployment
Please see the organizational deployment guide
2. Get the package into your environment
Option 1: Cached Package (Unreliable, Requires Internet - Same As Community)-
Open Source or Commercial:
- Proxy Repository - Create a proxy nuget repository on Nexus, Artifactory Pro, or a proxy Chocolatey repository on ProGet. Point your upstream to https://community.chocolatey.org/api/v2/. Packages cache on first access automatically. Make sure your choco clients are using your proxy repository as a source and NOT the default community repository. See source command for more information.
- You can also just download the package and push it to a repository Download
-
Open Source
-
Download the package:
Download - Follow manual internalization instructions
-
-
Package Internalizer (C4B)
-
Run: (additional options)
choco download ad-acl-scanner --internalize --source=https://community.chocolatey.org/api/v2/ -
For package and dependencies run:
choco push --source="'INTERNAL REPO URL'" - Automate package internalization
-
Run: (additional options)
3. Copy Your Script
choco upgrade ad-acl-scanner -y --source="'INTERNAL REPO URL'" [other options]See options you can pass to upgrade.
See best practices for scripting.
Add this to a PowerShell script or use a Batch script with tools and in places where you are calling directly to Chocolatey. If you are integrating, keep in mind enhanced exit codes.
If you do use a PowerShell script, use the following to ensure bad exit codes are shown as failures:
choco upgrade ad-acl-scanner -y --source="'INTERNAL REPO URL'"
$exitCode = $LASTEXITCODE
Write-Verbose "Exit code was $exitCode"
$validExitCodes = @(0, 1605, 1614, 1641, 3010)
if ($validExitCodes -contains $exitCode) {
Exit 0
}
Exit $exitCode
- name: Install ad-acl-scanner
win_chocolatey:
name: ad-acl-scanner
version: '8.3.0'
source: INTERNAL REPO URL
state: present
See docs at https://docs.ansible.com/ansible/latest/modules/win_chocolatey_module.html.
chocolatey_package 'ad-acl-scanner' do
action :install
source 'INTERNAL REPO URL'
version '8.3.0'
end
See docs at https://docs.chef.io/resource_chocolatey_package.html.
cChocoPackageInstaller ad-acl-scanner
{
Name = "ad-acl-scanner"
Version = "8.3.0"
Source = "INTERNAL REPO URL"
}
Requires cChoco DSC Resource. See docs at https://github.com/chocolatey/cChoco.
package { 'ad-acl-scanner':
ensure => '8.3.0',
provider => 'chocolatey',
source => 'INTERNAL REPO URL',
}
Requires Puppet Chocolatey Provider module. See docs at https://forge.puppet.com/puppetlabs/chocolatey.
4. If applicable - Chocolatey configuration/installation
See infrastructure management matrix for Chocolatey configuration elements and examples.
This package was approved as a trusted package on 26 May 2025.
AD ACL Scanner (Script)
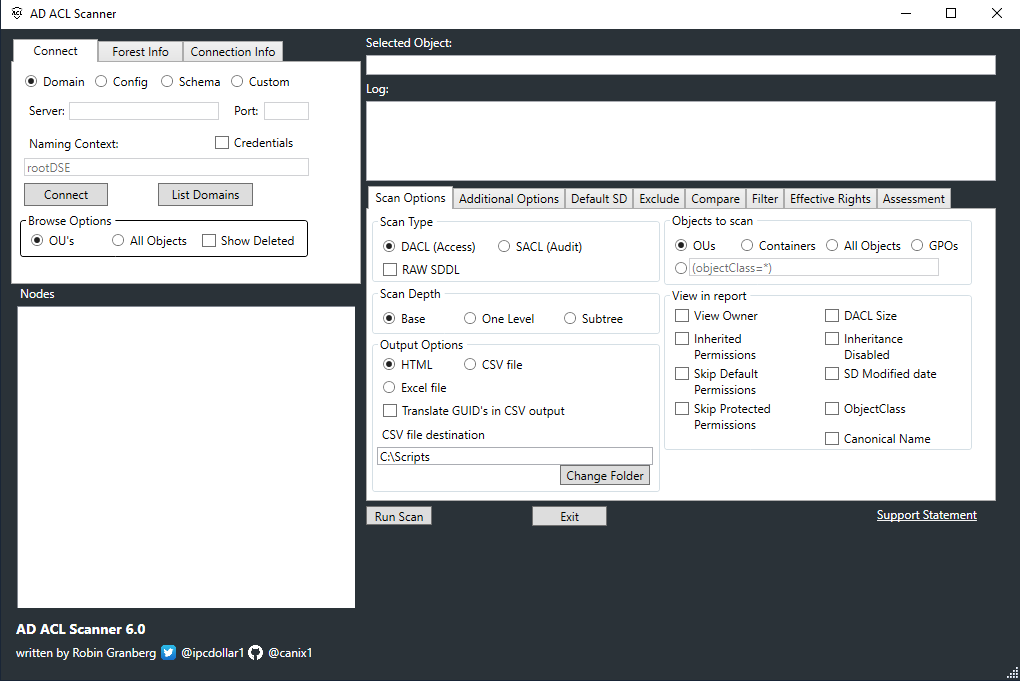
Features
It has the following features:
- View HTML reports of DACLs/SACLs and save it to disk.
- Export DACLs/SACLs on Active Directory objects in a CSV format.
- Connect and browse you default domain, schema , configuration or a naming context defined by distinguishedname.
- Browse naming context by clicking you way around, either by OU’s or all types of objects.
- Report only explicitly assigned DACLs/SACLs.
- Report on OUs , OUs and Container Objects or all object types.
- Filter DACLs/SACLs for a specific access type.. Where does “Deny” permission exists?
- Filter DACLs/SACLs for a specific identity. Where does "Domain\Client Admins" have explicit access? Or use wildcards like "jdoe".
- Filter DACLs/SACLs for permission on specific object. Where are permissions set on computer objects?
- Skip default permissions (defaultSecurityDescriptor) in report. Makes it easier to find custom permissions.
- Report owner of object.
- Compare previous results with the current configuration and see the differences by color scheme (Green=matching permissions, Yellow= new permissions, Red= missing permissions).
- Report when permissions were modified
- Can use AD replication metadata when comparing.
- Can convert a previously created CSV file to a HTML report.
- Effective rights, select a security principal and match it agains the permissions in AD.
- Color coded permissions based on criticality when using effective rights scan.
- List you domains and select one from the list.
- Get the size of the security descriptor (bytes).
- Rerporting on disabled inheritance .
- Get all inherited permissions in report.
- HTLM reports contain headers.
- Summary of criticality for all report types.
- Refresh Nodes by right-click container object.
- Exclude of objects from report by matching string to distinguishedName
- You can take a CSV file from one domain and use it for another. With replacing the old DN with the current domains you can resuse reports between domains. You can also replace the (Short domain name)Netbios name security principals.
- Reporting on modified default security descriptors in Schema.
- Verifying the format of the CSV files used in convert and compare functions.
- When compairing with CSV file Nodes missing in AD will be reported as "Node does not exist in AD"
- The progress bar can be disabled to gain speed in creating reports.
- If the fist node in the CSV file used for compairing can't be connected the scan will stop.
- Display group members in groups in the HTLM report.
- Present the value of the true SDDL in NTsecurityDescriptor, bypassing Object-Specific ACE merge done when a new instance of the ObjectSecurity class is initialized.
System requirements
- Powershell 3.0 or above
- PowerShell using a single-threaded apartment
- Some functions requires Microsoft .NET Framework version 4.0
choco://ad-acl-scanner
To use choco:// protocol URLs, install (unofficial) choco:// Protocol support
Package-specific issue
If this package isn't up-to-date for some days, Create an issue
Support the package maintainer and ![]()
Ms-PL
Microsoft Public License (Ms-PL)
This license governs use of the accompanying software. If you use the software, you accept this license. If you do not accept the license, do not use the software.
1. Definitions
The terms "reproduce," "reproduction," "derivative works," and "distribution" have the same meaning here as under U.S. copyright law.
A "contribution" is the original software, or any additions or changes to the software.
A "contributor" is any person that distributes its contribution under this license.
"Licensed patents" are a contributor's patent claims that read directly on its contribution.
2. Grant of Rights
(A) Copyright Grant- Subject to the terms of this license, including the license conditions and limitations in section 3, each contributor grants you a non-exclusive, worldwide, royalty-free copyright license to reproduce its contribution, prepare derivative works of its contribution, and distribute its contribution or any derivative works that you create.
(B) Patent Grant- Subject to the terms of this license, including the license conditions and limitations in section 3, each contributor grants you a non-exclusive, worldwide, royalty-free license under its licensed patents to make, have made, use, sell, offer for sale, import, and/or otherwise dispose of its contribution in the software or derivative works of the contribution in the software.
3. Conditions and Limitations
(A) No Trademark License- This license does not grant you rights to use any contributors' name, logo, or trademarks.
(B) If you bring a patent claim against any contributor over patents that you claim are infringed by the software, your patent license from such contributor to the software ends automatically.
(C) If you distribute any portion of the software, you must retain all copyright, patent, trademark, and attribution notices that are present in the software.
(D) If you distribute any portion of the software in source code form, you may do so only under this license by including a complete copy of this license with your distribution. If you distribute any portion of the software in compiled or object code form, you may only do so under a license that complies with this license.
(E) The software is licensed "as-is." You bear the risk of using it. The contributors give no express warranties, guarantees or conditions. You may have additional consumer rights under your local laws which this license cannot change. To the extent permitted under your local laws, the contributors exclude the implied warranties of merchantability, fitness for a particular purpose and non-infringement.VERIFICATION
Verification is intended to assist the Chocolatey moderators and community
in verifying that this package's contents are trustworthy.
The embedded software has been downloaded from the listed download
location on and can be verified by doing the following:
1. Download the following:
url: <https://github.com/canix1/ADACLScanner/releases/download/8.3/ADACLScan.ps1>
2. You can obtain the checksum using one of the following methods:
- Use powershell function 'Get-FileHash'
- Use Chocolatey utility 'checksum.exe'
checksum type: sha256
checksum: E7E5E1E9600326E8C9F0E3816A69BAF1D55B9EC26CA6E01ED6F75562E9AE5869
Using AU:
Get-RemoteChecksum
$ErrorActionPreference = 'Stop'
$packageName = 'ad-acl-scanner'
$shortcutName = 'AD ACL Scanner'
Remove-Item "$ENV:USERPROFILE\Desktop\$shortcutName.lnk" -Force -ErrorAction SilentlyContinue
Log in or click on link to see number of positives.
In cases where actual malware is found, the packages are subject to removal. Software sometimes has false positives. Moderators do not necessarily validate the safety of the underlying software, only that a package retrieves software from the official distribution point and/or validate embedded software against official distribution point (where distribution rights allow redistribution).
Chocolatey Pro provides runtime protection from possible malware.
| Add to Builder | Version | Downloads | Last Updated | Status |
|---|---|---|---|---|
| AD ACL Scanner (Script) 8.3.0 | 42 | Monday, May 26, 2025 | Approved | |
| AD ACL Scanner (Script) 8.2.0 | 33 | Saturday, May 24, 2025 | Approved | |
| AD ACL Scanner (Script) 8.1.0 | 26 | Wednesday, May 21, 2025 | Approved | |
| AD ACL Scanner (Script) 8.0.0 | 65 | Sunday, April 13, 2025 | Approved | |
| AD ACL Scanner (Script) 7.9.0 | 185 | Monday, July 1, 2024 | Approved | |
| AD ACL Scanner (Script) 6.8 | 630 | Saturday, February 5, 2022 | Approved | |
| AD ACL Scanner (Script) 6.4 | 222 | Monday, May 24, 2021 | Approved | |
| AD ACL Scanner (Script) 5.9 | 720 | Wednesday, November 13, 2019 | Approved | |
| AD ACL Scanner (Script) 5.6.3 | 428 | Friday, June 14, 2019 | Approved | |
| AD ACL Scanner (Script) 5.6.2 | 295 | Friday, April 5, 2019 | Approved | |
| AD ACL Scanner (Script) 5.6.1 | 360 | Wednesday, January 2, 2019 | Approved | |
| AD ACL Scanner (Script) 5.6 | 467 | Friday, April 6, 2018 | Approved | |
| AD ACL Scanner (Script) 5.5 | 472 | Sunday, November 26, 2017 | Approved | |
| AD ACL Scanner (Script) 5.4.4 | 469 | Friday, September 22, 2017 | Approved | |
| AD ACL Scanner (Script) 5.4.3 | 435 | Friday, September 1, 2017 | Approved |
Robin Granberg
-
- dotnet4.0 (≥ 4.0.0)
- powershell (≥ 3.0.0)
Ground Rules:
- This discussion is only about AD ACL Scanner (Script) and the AD ACL Scanner (Script) package. If you have feedback for Chocolatey, please contact the Google Group.
- This discussion will carry over multiple versions. If you have a comment about a particular version, please note that in your comments.
- The maintainers of this Chocolatey Package will be notified about new comments that are posted to this Disqus thread, however, it is NOT a guarantee that you will get a response. If you do not hear back from the maintainers after posting a message below, please follow up by using the link on the left side of this page or follow this link to contact maintainers. If you still hear nothing back, please follow the package triage process.
- Tell us what you love about the package or AD ACL Scanner (Script), or tell us what needs improvement.
- Share your experiences with the package, or extra configuration or gotchas that you've found.
- If you use a url, the comment will be flagged for moderation until you've been whitelisted. Disqus moderated comments are approved on a weekly schedule if not sooner. It could take between 1-5 days for your comment to show up.









 Ansible
Ansible

 PS DSC
PS DSC
