
Downloads:
571
Downloads of v 1.4.4:
312
Last Update:
02 Jun 2021
Package Maintainer(s):
Software Author(s):
- Neo23x0
Tags:
- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
Raccine
- 1
- 2
- 3
1.4.4 | Updated: 02 Jun 2021
- Software Specific:
- Software Site
- Software Source
- Software License
- Software Docs
- Software Issues
- Package Specific:
- Package Source
- Package outdated?
- Package broken?
- Contact Maintainers
- Contact Site Admins
- Software Vendor?
- Report Abuse
- Download
Downloads:
571
Downloads of v 1.4.4:
312
Maintainer(s):
Software Author(s):
- Neo23x0
Raccine 1.4.4
Legal Disclaimer: Neither this package nor Chocolatey Software, Inc. are affiliated with or endorsed by Neo23x0. The inclusion of Neo23x0 trademark(s), if any, upon this webpage is solely to identify Neo23x0 goods or services and not for commercial purposes.
- 1
- 2
- 3
This Package Contains an Exempted Check
Not All Tests Have Passed
Deployment Method: Individual Install, Upgrade, & Uninstall
To install Raccine, run the following command from the command line or from PowerShell:
To upgrade Raccine, run the following command from the command line or from PowerShell:
To uninstall Raccine, run the following command from the command line or from PowerShell:
Deployment Method:
This applies to both open source and commercial editions of Chocolatey.
1. Enter Your Internal Repository Url
(this should look similar to https://community.chocolatey.org/api/v2/)
2. Setup Your Environment
1. Ensure you are set for organizational deployment
Please see the organizational deployment guide
2. Get the package into your environment
Option 1: Cached Package (Unreliable, Requires Internet - Same As Community)-
Open Source or Commercial:
- Proxy Repository - Create a proxy nuget repository on Nexus, Artifactory Pro, or a proxy Chocolatey repository on ProGet. Point your upstream to https://community.chocolatey.org/api/v2/. Packages cache on first access automatically. Make sure your choco clients are using your proxy repository as a source and NOT the default community repository. See source command for more information.
- You can also just download the package and push it to a repository Download
-
Open Source
-
Download the package:
Download - Follow manual internalization instructions
-
-
Package Internalizer (C4B)
-
Run: (additional options)
choco download raccine --internalize --source=https://community.chocolatey.org/api/v2/ -
For package and dependencies run:
choco push --source="'INTERNAL REPO URL'" - Automate package internalization
-
Run: (additional options)
3. Copy Your Script
choco upgrade raccine -y --source="'INTERNAL REPO URL'" [other options]See options you can pass to upgrade.
See best practices for scripting.
Add this to a PowerShell script or use a Batch script with tools and in places where you are calling directly to Chocolatey. If you are integrating, keep in mind enhanced exit codes.
If you do use a PowerShell script, use the following to ensure bad exit codes are shown as failures:
choco upgrade raccine -y --source="'INTERNAL REPO URL'"
$exitCode = $LASTEXITCODE
Write-Verbose "Exit code was $exitCode"
$validExitCodes = @(0, 1605, 1614, 1641, 3010)
if ($validExitCodes -contains $exitCode) {
Exit 0
}
Exit $exitCode
- name: Install raccine
win_chocolatey:
name: raccine
version: '1.4.4'
source: INTERNAL REPO URL
state: present
See docs at https://docs.ansible.com/ansible/latest/modules/win_chocolatey_module.html.
chocolatey_package 'raccine' do
action :install
source 'INTERNAL REPO URL'
version '1.4.4'
end
See docs at https://docs.chef.io/resource_chocolatey_package.html.
cChocoPackageInstaller raccine
{
Name = "raccine"
Version = "1.4.4"
Source = "INTERNAL REPO URL"
}
Requires cChoco DSC Resource. See docs at https://github.com/chocolatey/cChoco.
package { 'raccine':
ensure => '1.4.4',
provider => 'chocolatey',
source => 'INTERNAL REPO URL',
}
Requires Puppet Chocolatey Provider module. See docs at https://forge.puppet.com/puppetlabs/chocolatey.
4. If applicable - Chocolatey configuration/installation
See infrastructure management matrix for Chocolatey configuration elements and examples.
Private CDN cached downloads available for licensed customers. Never experience 404 breakages again! Learn more...
This package was approved by moderator mwallner on 13 Jul 2021.

Raccine
A Simple Ransomware Protection
Why
We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let's try to create a simple vaccine.
How it works
We register a debugger for vssadmin.exe (and wmic.exe), which is our compiled raccine.exe. Raccine is a binary, that first collects all PIDs of the parent processes and then tries to kill all parent processes.
Avantages:
- The method is rather generic
- We don't have to replace a system file (
vssadmin.exeorwmic.exe), which could lead to integrity problems and could break our raccination on each patch day - Flexible YARA rule scanning of command line params for malicious activity
- The changes are easy to undo
- Runs on Windows 7 / Windows 2008 R2 or higher
- No running executable or additional service required (agent-less)
Disadvantages / Blind Spots:
- The legitimate use of
vssadmin.exe delete shadows(or any other blacklisted combination) isn't possible anymore - It even kills the processes that tried to invoke
vssadmin.exe delete shadows, which could be a backup process - This won't catch methods in which the malicious process isn't one of the processes in the tree that has invoked
vssadmin.exe(e.g. viaschtasks)
Example
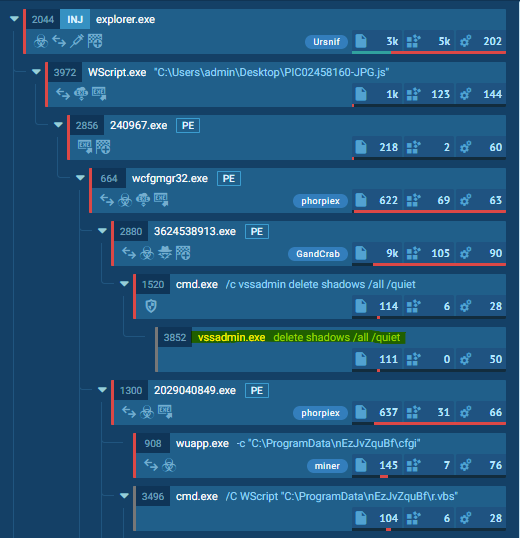
Emotet without Raccine - Link
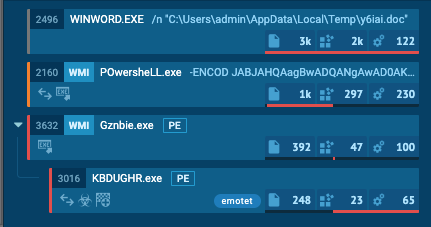
Emotet with Raccine - Link (ignore the process activity that is related to the Raccine installation)
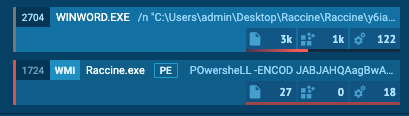
The infection gets nipped in the bud.
Warning !!!
USE IT AT YOUR OWN RISK!
You won't be able to run commands that use the blacklisted commands on a raccinated machine anymore until your apply the uninstall patch raccine-reg-patch-uninstall.reg. This could break various backup solutions that run that specific command during their work. It will not only block that request but kills all processes in that tree including the backup solution and its invoking process.
If you have a solid security monitoring that logs all process executions, you could check your logs to see if vssadmin.exe delete shadows, vssadmin.exe resize shadowstorage ... or the other blocked command lines are frequently or sporadically used for legitimate purposes in which case you should refrain from using Raccine.
Please Note This is an automatically updated package. If the package is outdated for more than two days, please let me know.
$installer = "\tools\Raccine\install-raccine.bat"
Start-Process -FilePath "$env:ChocolateyPackageFolder$installer" -ArgumentList @("UNINSTALL")
Log in or click on link to see number of positives.
- raccine.1.4.4.nupkg (b594f791bc46) - ## / 59
- Raccine.zip (8b8524d99c41) - ## / 61
In cases where actual malware is found, the packages are subject to removal. Software sometimes has false positives. Moderators do not necessarily validate the safety of the underlying software, only that a package retrieves software from the official distribution point and/or validate embedded software against official distribution point (where distribution rights allow redistribution).
Chocolatey Pro provides runtime protection from possible malware.
| Add to Builder | Version | Downloads | Last Updated | Status |
|---|---|---|---|---|
| Raccine 1.4.4 | 312 | Wednesday, June 2, 2021 | Approved | |
| Raccine 1.4.3 | 118 | Saturday, May 29, 2021 | Approved | |
| Raccine 1.4.1 | 141 | Friday, March 19, 2021 | Approved |
Florian Roth
Ground Rules:
- This discussion is only about Raccine and the Raccine package. If you have feedback for Chocolatey, please contact the Google Group.
- This discussion will carry over multiple versions. If you have a comment about a particular version, please note that in your comments.
- The maintainers of this Chocolatey Package will be notified about new comments that are posted to this Disqus thread, however, it is NOT a guarantee that you will get a response. If you do not hear back from the maintainers after posting a message below, please follow up by using the link on the left side of this page or follow this link to contact maintainers. If you still hear nothing back, please follow the package triage process.
- Tell us what you love about the package or Raccine, or tell us what needs improvement.
- Share your experiences with the package, or extra configuration or gotchas that you've found.
- If you use a url, the comment will be flagged for moderation until you've been whitelisted. Disqus moderated comments are approved on a weekly schedule if not sooner. It could take between 1-5 days for your comment to show up.









 Ansible
Ansible

 PS DSC
PS DSC
